The storage and safe administration of knowledge and passwords is among the most vital points within the crypto and blockchain world, and extra usually in all on-line environments.
Encryption, intense because the artwork of “hidden writings” able to changing plain textual content into encrypted textual content and vice versa, involves our help making it tough for hackers to permit unauthorized entry to sure networks and transactions.
Let’s delve into the totally different strategies by which encryption can shield invaluable data and safeguard passwords.
Symmetric and uneven password encryption within the crypto sector
Usually when speaking about password safety in cryptography, reference is made to 2 encryption strategies: symmetric and uneven.
That symmetric one refers to a sort of textual content encryption that makes use of a single key to encrypt and decrypt data:
The encryption secret is shared between sender and recipient and is normally agreed upon upfront: it represents the central aspect that in cryptocurrencies permits customers to entry and handle their digital assets.
Symmetric encryption with a single key is among the most typical means to guard passwords, transactions, and communication between working nodes.
When performing, for instance, a funds switch from one pockets to a different, it ensures that the knowledge is learn and shared solely by two events concerned within the transaction, conserving the information protected from prying eyes.
Nonetheless, regardless of the benefits it brings, symmetric encryption has limitations when it comes to scalability and key administration.
Certainly, the necessity for communication in pairs tremendously limits the enlargement of this follow in a system with many extra customers. On the identical time, extra customers indicate human errors within the administration and conservation of the so-called “personal key”, which if misplaced results in the lack of crypto or knowledge saved within the digital pockets.
To beat these limitations, uneven cryptography involves our help by offering a pair of separate keys (private and non-private) within the encoding and decoding of passwords.
This extra stage of safety immediately will increase knowledge safety: the general public key will be shared with anybody on any community (like once we share our deal with to obtain a cost in crypto), whereas the personal key have to be stored secret.
Each keys are generated by an algorithm that makes use of massive prime numbers to create two distinctive and mathematically linked keys.
Anyway, whoever possesses the general public key can encrypt a message, however solely the holder of the personal counterpart can decrypt the textual content. We are able to think about this as if it have been an e-mail inbox: whoever holds the general public key can ship a message, however solely the proprietor of the personal key can open the e-mail and browse the messages.
Non-custodial software program wallets like Belief Pockets or MetaMask use uneven cryptography to supply the best potential safety to their customers.
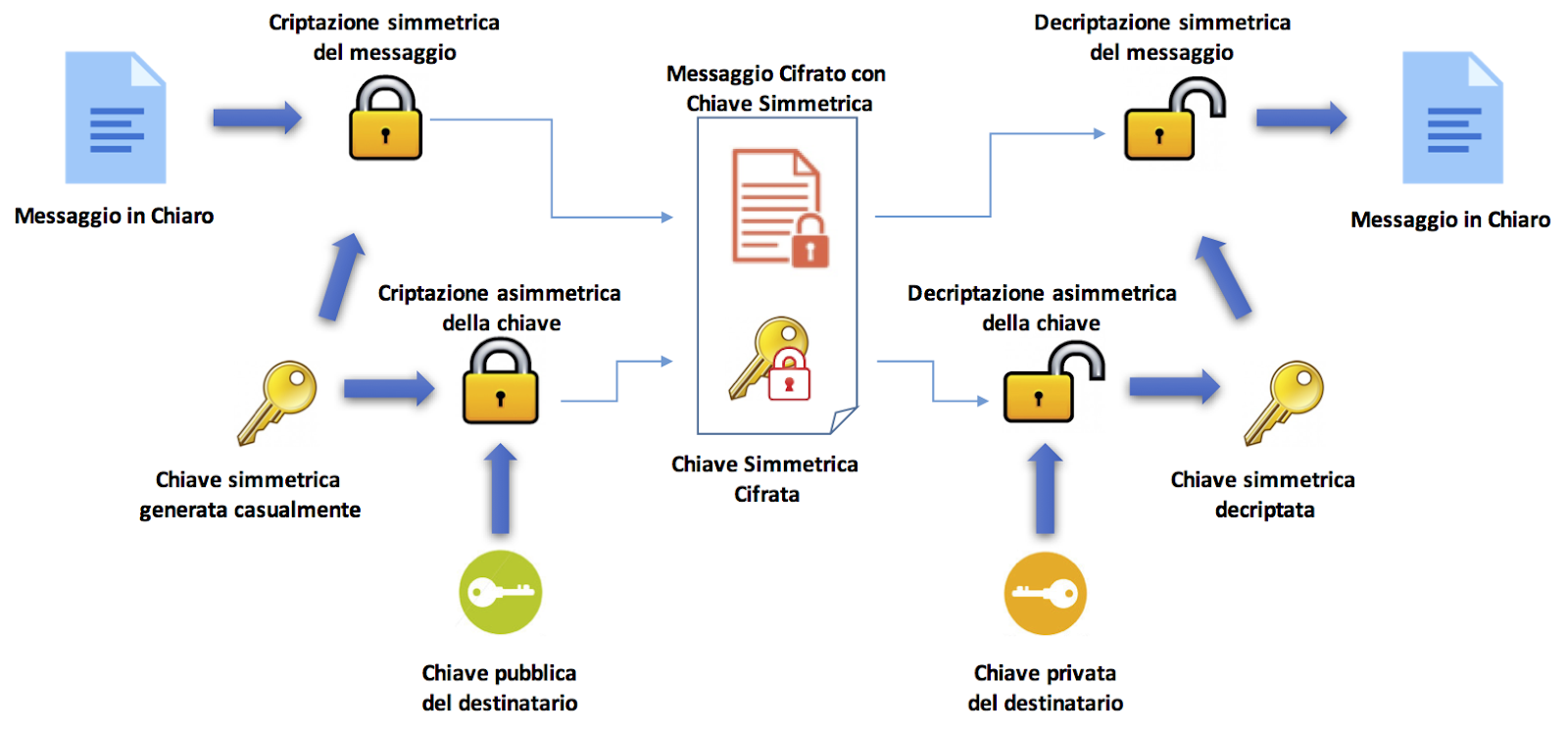
Supply: https://www.javaboss.it/crittografia-in-java/
The commonest codecs of encrypted passwords
Password encryption within the crypto and blockchain sector happens in line with totally different codecs that can be utilized for various functions and supply totally different ranges of safety:
- MD5 (Message Digest 5):
The MD5 algorithm, developed by Ronald Rivest in 1991, generates a 128-bit hash (32 hexadecimal characters) from a variable-length enter.
It’s not thought-about safe resulting from vulnerabilities found in its algorithm. Nonetheless, it’s nonetheless utilized in some legacy contexts, for instance to confirm the integrity of recordsdata.
- SHA-1 (Safe Hash Algorithm 1):
SHA-1 generates a 160-bit hash (40 hexadecimal characters).
It’s not thought-about as safe because it as soon as was, having proven a number of vulnerabilities: it’s now usually changed by extra sturdy algorithms similar to SHA-256 and SHA-3. Nonetheless, it’s nonetheless utilized in a variety of techniques and new purposes.
- Salt:
The salt is a random sequence of bits that’s added to the password earlier than calculating the hash.
It solves the issue of collisions (two totally different passwords producing the identical hash) in hashing strategies.
By including a salt, even an identical passwords may have fully totally different hashes. This makes it more durable for attackers to decrypt passwords by brute drive assaults.
- Bcrypt:
Bcrypt is a hashing algorithm particularly designed for password encryption.
Use a salt and quite a few iterations to decelerate the hash calculation. It’s extensively used to guard consumer passwords within the area of databases.
The selection of encryption format is determined by the precise wants of the reference system. These days, it’s advisable to make use of hashing algorithms similar to bcrypt or SHA-2 to guard passwords and mitigate cyber assaults.
Hash features and digital signatures
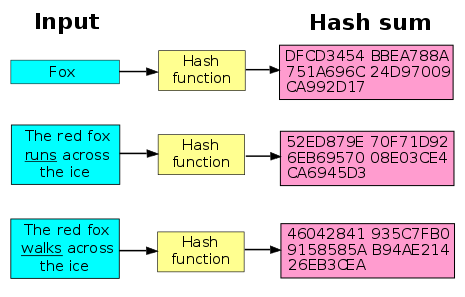
One other option to shield passwords and invaluable data in cryptocurrencies is to depend on hash features, that’s algorithms that rework any type of knowledge right into a string of characters of fastened size.
By utilizing sturdy hashing algorithms, we are able to successfully shield delicate data and forestall cyber assaults.
Hash features are irreversible: it isn’t potential to transform a hash again into its authentic knowledge. They’re important in knowledge administration on the blockchain as a result of they permit structuring data with out compromising its preliminary integrity
Hashes can even act as fingerprints for all encrypted passwords, defending the consumer towards unauthorized actions on their account.
Certainly, any modification to the unique knowledge would end in a brand new hash, which might not correspond to the unique supply and subsequently wouldn’t be verifiable on the blockchain.
One other methodology to make sure password safety, and extra particularly the authenticity and integrity of knowledge in a message, is to make use of the so-called “digital signatures” (uneven cryptography approach).
That is merely a way to make sure that the proprietor of these particular knowledge is approving the transaction. Usually, the sender creates the digital signature utilizing a personal key to encrypt the signature knowledge, whereas the recipient obtains the signer’s public key to decrypt the information. This code represents irrefutable proof {that a} message has been created solely by the sender and has not been tampered with on-line.
When speaking about digital signatures, one instantly thinks of signature units like Ledger, Trezor, and Bitbox that permit to validate a transaction earlier than it’s broadcasted to the remainder of a cryptographic community.
Nonetheless, watch out to not think about these units as wallets: they don’t comprise your cryptocurrencies however solely assist you to approve the transactions essential to spend them.
We frequently say, “my crypto is ON my Ledger”.
However your digital belongings aren’t truly saved bodily in your Ledger – they’re on the blockchain.
Your Ledger shops and protects your personal keys and retains them protected so you’ll be able to totally personal and handle your belongings.@iancr explains: pic.twitter.com/PGrmQIvKpV
— Ledger (@Ledger) Could 11, 2023

