Disclosure: The views and opinions expressed right here belong solely to the writer and don’t characterize the views and opinions of the crypto.information essential article.
Final November, DEX aggregator KyberSwap was hacked to the tune of $47 million, inflicting the protocol to be compromised and the funds of its liquidity suppliers to be misplaced. In an odd flip of occasions, the mysterious hacker made an unprecedented request that the stolen cash be launched provided that all the administration workforce resigned and appointed him CEO. Unsurprisingly, this demand was rejected and the hacker started transferring the stolen funds to Ethereum utilizing the Synapse protocol.
You may also like: Spot Bitcoin ETFs are right here. What’s subsequent? Regulate defi? | Opinion
KyberSwap barely survived the incident, slicing half its workforce as its total worth fell by 68 p.c. As with all defi hacks, this one is unlucky, however there’s a silver lining.
In comparison with the early days of the crypto winter, worth loss from defi hacks fell 64 p.c in 2023, with the typical loss per hack falling 7.5 p.c, in accordance with knowledge from Chainalysis. That is clearly a constructive growth and a testomony to the general progress of the defi area and progress in safety. Bridges – blockchain protocols that promote cross-chain interoperability – have contributed to defi’s expanded capabilities by unlocking remoted ‘islands’ of liquidity, permitting property to circulation extra freely.
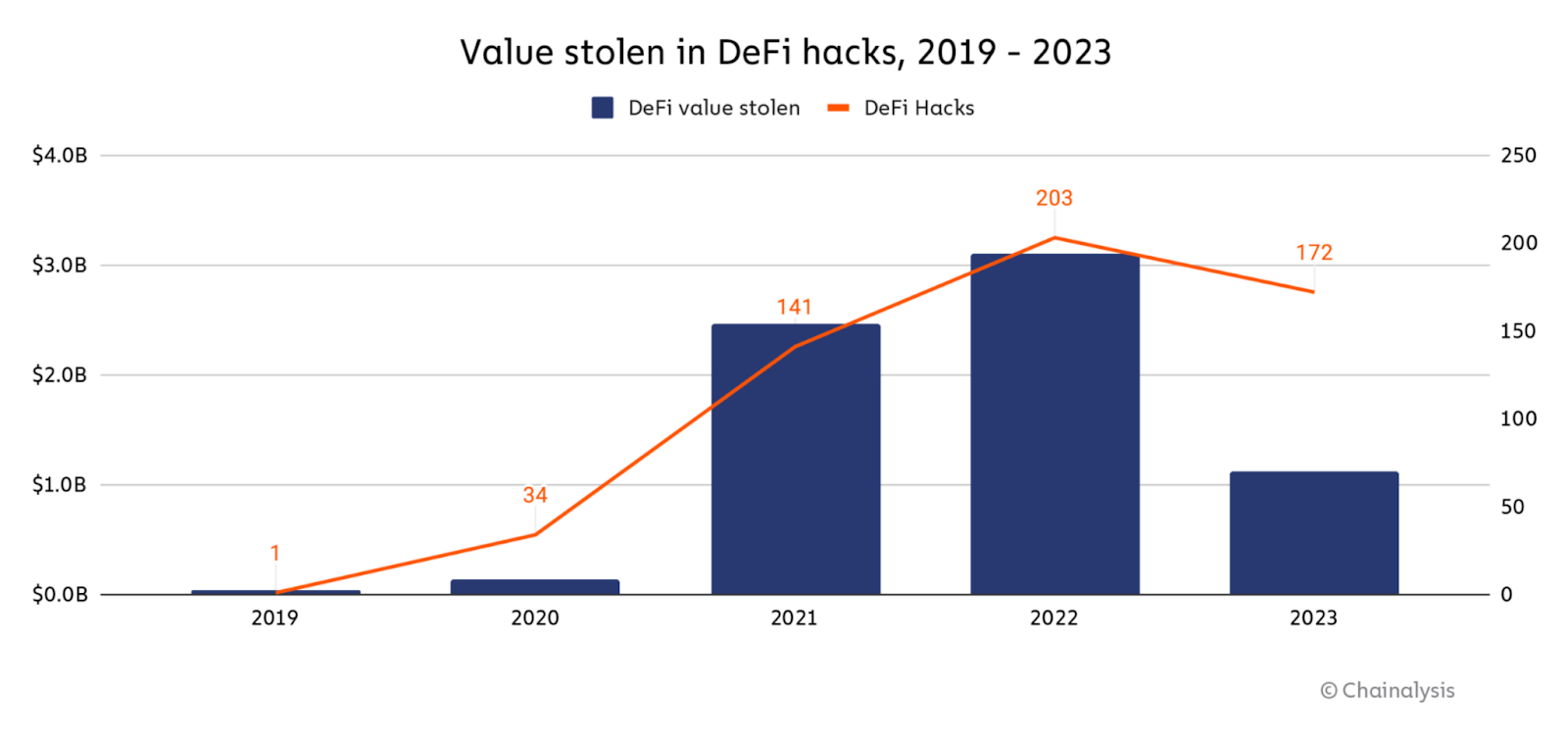
The worth misplaced in defi hacks | Supply: Chain evaluation
Bridges additionally drive innovation by permitting builders to discover new methods to leverage cross-chain capabilities. We are able to see this by way of the creation of latest monetary merchandise, improved scalability, improved privateness options, simpler collaboration measures and versatile threat administration.
Regardless of the decline in safety breaches and the rise in bridge-based defi innovation, blockchain interoperability continues to be fairly restricted. Reasonably than selling common interoperability, every cross-chain protocol or bridge represents a hyperlink between two blockchain networks, which means true interoperability would require a fancy net of quite a few protocols connecting every blockchain.
This presents its personal set of safety challenges. Regardless of the decline in hacks, the defi area continues to be flooded with hackers on the lookout for potential flaws in a protocol or a wise contract vulnerability that they’ll exploit. Since most bridges depend on good contracts, count on hackers to proceed testing them, whether or not it is a centralized change, a layer-2 chain, or a set of oracles hosted by a third-party server .
Inherent safety challenges, particularly on unregulated bridges, are nearly inconceivable to utterly get rid of as a result of most bridges talk with exterior techniques, making them prone to hacking or tampering. Customers transferring property between disparate blockchain networks through a trusted or untrusted bridge should weigh critical safety considerations.
Generally, trusted bridges just like the Binance Bridge provide simplicity and compliance on the expense of centralization by way of an exterior entity. Confidential bridges, alternatively, prioritize decentralization, safety, and permissionless entry, however their reliance on good contracts supplies hackers with a transparent assault vector.
Nonetheless, each kinds of bridges may be exploited. Moreover, the overall lack of KYC and AML protocols at most bridges makes them a hacker’s finest buddy when he wants to scrub away stolen funds. As a result of bridges are essentially the most accessible and accessible mechanism for breaking down the limitations between remoted blockchains, defi builders and customers ought to proceed with warning when utilizing a cross-chain protocol.
The selection between dependable and trusted bridges comes right down to the precise use case, necessities, and tradeoffs that builders or customers prioritize or are keen to just accept. A median web3 consumer who desires to switch cash from one pockets to a different can go for a trusted bridge for its simplicity, pace and decrease fuel prices. Nonetheless, a dApp developer might choose a dependable bridge to take care of full management over their property inside a decentralized surroundings.
When bridging property, the security issue is commonly taken with no consideration. Whereas each trusted and trusted bridges can adhere to various ranges of compliance and threat mitigation (or cast off them altogether), utilizing a bridge with a strong compliance layer actually has its advantages.
Let’s return to the KyberSwap hack to higher perceive the potential implications of those safety dangers.
By analyzing the on-chain knowledge, it turns into clear that if the Synapse protocol had carried out a compliance layer, the hacker would by no means have been capable of route the property to an Ethereum-based pockets and get out. A threat mitigation platform with an end-to-end compliance module may be utilized to any dApp or protocol and reject probably problematic transactions, comparable to transferring thousands and thousands in stolen funds.
Danger mitigation is now not a “bonus function” that tasks can ignore. As regulatory our bodies contemplate extra complete legal guidelines, compliance with them will change into more and more vital, particularly as conventional monetary establishments proceed to flirt with offering defi companies to their clients.
It is vital to notice that including a compliance layer to any decentralized protocol just isn’t about censorship or thwarting crypto’s core ethos of economic freedom and eradicating middlemen. Reasonably, it’s solely about defending consumer property from being hijacked by criminals, terrorist supporters, and different dangerous actors.
Because the crypto world strives for wider adoption, the necessity for compliance mechanisms is extra vital than ever. With assault vectors continuously evolving, hacks and thieves will proceed to threaten the integrity of all the trade and undermine the aim of mainstream adoption.
Whereas bridges will not allow common interoperability throughout the huge blockchain ecosystem, good compliance can scale back threat for customers and builders and safeguard defi progress. Subsequently, builders could be clever to contemplate a bridge’s compliance requirements when conducting cross-chain transactions.
Learn extra: Runes makes Bitcoin enjoyable and accessible once more | Opinion
Man Vider
Man Vider is the co-founder and CTO of Kima, a decentralized blockchain-based cash switch protocol. Man’s background consists of greater than two and a half a long time of growth management with roles at Yahoo, ADP, BMC, Blue Cross/Blue Defend and Fisker Automotive. As well as, Man has co-founded three startups and held advisory positions in deep tech and web3 tasks. In recent times he has honed his experience within the discipline of fintech and blockchain. Man’s previous entrepreneurial ventures embody Amodello, the primary AR app for house design in 2010, and ExPOS, a knowledge analytics device for the hospitality trade in 2012.

